- Ahnlab Magniber Decrypt V4 11
- Ahnlab Magniber Decrypt V4 12
- Ahnlab Magniber Decrypt V4 1 Download
- Ahnlab Magniber Decrypt V4 10
What is the Magniber virus?
Ahnlab Magniber Decrypt V4 11
The Magniber virus is ransomware that encrypts files using cryptography ciphers, appends the .ihsdj and .kgpvwnr file extensions to the end of the file names, and downloads a ransom note named READ_ME_FOR_DECRYPT_[id].txt throughout the infected computer. This computer virus is known to be the successor to Cerber.
- AhnLab 보안 제품과 서비스 구성을 한. (Magniber) 랜섬웨어, 크립트엑스엑스엑스(CryptXXX) 3.x 버전, 2.x 버전, 나부커(Nabucur), 테슬라크립트(TeslaCrypt)의 일부이며, 신∙변종.
- AhnLab Security Emergency response Center. – Update (2018.08.30) The “오토캐드2014키젠.js” (translation: AutoCAD2014keygen.js) file as of August 30 was discovered with download feature via powershell removed, as shown in the script code below.
- Magniber 랜섬웨어와 외형이 유사한 형태의 랜섬웨어로는 Hermes 와 GandCrab 랜섬웨어가 있다. 즉, V3 에서 “Trojan/Win32.Magniber” 로 진단하는 파일 중에는 실제 Magniber 가 아닌 유형이 존재할 수 있다. 각 랜섬웨어 별 랜섬노트를 통해 구분이 가능하다. § Hermes: DECRYPTINFORMATION.
Magniber ransomware has shown rapid development during the past several years. Being introduced in Korea for the first time in mid-2017, its number skyrocketed by April 2018. Despite its exponential growth, leading cybersecurity companies, such as AhnLab, promptly released restoration tools, resulting in the downfall of Magniber.
Once the Magniber virus has encrypted files it will download the ransom note in attempt to gather a ransom. The ransom note explains what happened and how to obtain bitcoins to purcahse a decryption key and special tool to decrypt files the way that the malware authors want them to.
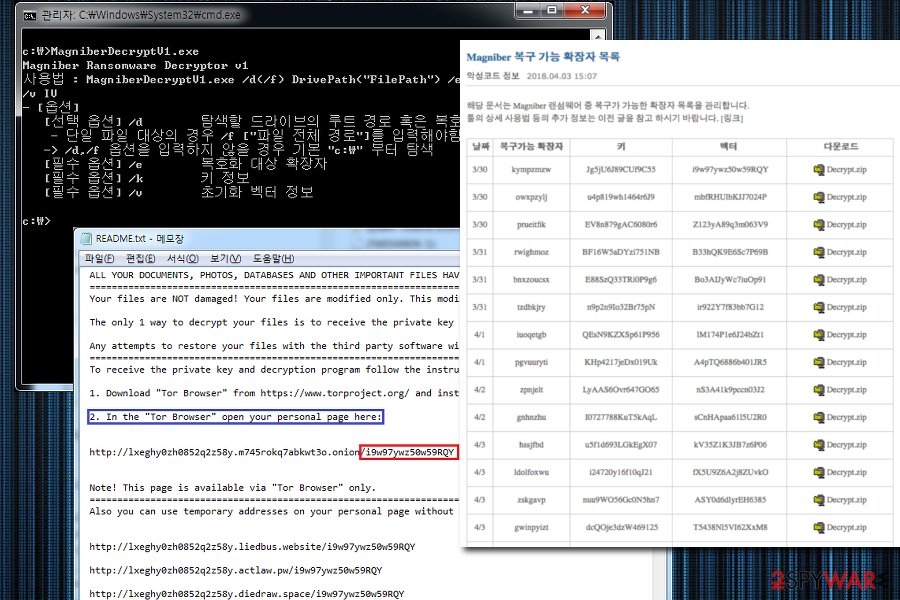
Here’s an example of one of the ransom notes used by Magniber ransomware:
ALL Y0UR D0CUMENTS, PHOTOS, DATABASES AND OTHER IMP0RTANT FILES HAVE BEEN ENCRYPTED!
Your files are NOT damaged! Your files are modified only. This modification is reversible.
The only 1 way to decrypt your files is to receive the private key and decryption program.
Any attempts to restore your files with the third-party software will be fatal for your files!
To receive the private key and decryption program follow the instructions below:
1. Download “Tor Browser” from https://www.torproject.org/ and install it.
2. In the “Tor Browser” open your personal page here:
http://[victim_id].ofotqrmsrdc6c3rz.onion/EP866p5M93wDS513
Note! This page is available via “Tor Browser” only.
Also you can use temporary addresses on your personal page without using “Tor Browser”:
http://[victim_id].bankme.date/EP866p5M93wDS513
http://[victim_id].jobsnot.services/EP866p5M93wDS513
http://[victim_id].carefit.agency/EP866p5M93wDS513
http://[victim_id].hotdisk.world/EP866p5M93wDS513
Note! These are temporary addresses! They will be available for a limited amount of time!
How did Magniber get on my computer?
Like most ransomware infections, the Magniber virus is typically distrubyted by email spam messages that contain malicious 7zip, 7z, rar, docx, and zip email attachments. Once the attachment is downloaded and executed it will spread the malware across the machine and begin its encryption process.
How to remove Magniber (Removal Guide)
The Magniber removal guide on this page explains how to remove Magniber virus, ransomware, malware, and decrypt encrypted files. Follow each step below to remove this infection and secure your computer from malicious threats. On the bottom of this guide you will also find recovery and decryption software for various ransomware infections.
1. Remove Magniber virus with Malwarebytes
- Open your browser window and download Malwarebytes 3.0 Premium or Malwarebytes Anti-Malware Free.
- Open the executable file (mb3-setup.exe) to begin installing Malwarebytes.
- Select your language, click Next, then select “I accept the agreement,” click the Next button several times, and then click the Install button to install Malwarebytes. Click Finish once the install process is complete.
- Open Malwarebytes and click the Scan Now button on the Dashboard to begin scanning your computer.
- Click the Quarantine Selected button once the scan is finished.
- If Malwarebytes says “All selected items have been removed successfully. A log file has been saved to the logs folder. Your computer needs to be restarted to complete the removal process. Would you like to restart now?” click the Yes button to restart your computer.
2. Remove trace files with HitmanPro
- Open your browser window and download HitmanPro.
- Open the executable file (hitmanpro_x64.exe or hitmanpro_x32.exe) to begin installing HitmanPro.
- Click the Next button, check “I accept the terms of the license agreement,” and click the Next button again.
- On the Setup page select “Yes, create a copy of HitmanPro so I can regularly scan this computer (recommended)” and add your email address to the registration fields to begin the free trial.
- Click Next to begin scanning your computer.
- Once the Scan results are displayed click the Next button and click the Next button again on the Removal results page.
3. Clean up and repair issues with CCleaner
Ahnlab Magniber Decrypt V4 12
- Open your browser window and download CCleaner Professional or CCleaner Free.
- Open the executable file (ccsetup.exe or other) to begin installing CCleaner.
- Click the Install button to begin stalling the program.
- Click Run CCleaner to open the program when installation is complete.
- Select the Cleaner tab and click the Analyze button.
- When the Analyze process is complete click the Run Cleaner button to clean all files.
- Next, select the Registry tab and click the Scan for Issues button to scan for issues in your registry.
- When the scan is complete click the Fix selected Issues button and Fix All Selected Issues button to fix the issues.
- Next, select the Tools tab and click Startup. Examine each area, search for suspicious entries, and delete any suspicious startup entries by selecting the entry and clicking the Delete button.
- Next, click Browser Plugins and search each internet browser for unwanted browser add-ons and extensions. Click the extension you want to delete and click the Delete button to remove it.
File Recovery Software
| NAME | DESCRIPTION | DOWNLOAD |
|---|---|---|
| Shadow Explorer | Restores lost or damaged files from Shadow Copies | Download (Free) |
| Photorec | Recovers lost files | Download (Free) |
| Recuva | Recovers lost files | Download (Free) | Buy |
Troubleshoot

Alternative methods are suggested if there are issues removing Magniber ransomware from an infected computer.
How to Restore your computer
If a restore point has previously been established on your machine you will be able to perform a system restore in order to restore your machine to a date and time before it was infected. You will lose files on your computer that were obtained prior to the restore point.
There are several options to restore your computer. Most computers have their own restore software that can be found by performing a search. Additionally, computers that run the Windows Operating System have a default restore program that can also be found by performing a search.
A boot screen that can be used to access options to restore your computer can be reached by rebooting your computer and pressing the F8 key once the manufacture screen is displayed.
How to Recover your computer to factory settings
Ahnlab Magniber Decrypt V4 1 Download
A system recovery (or reset) will recover your computer to factory settings. You will lose the current programs and files on your computer.
There are several options to recover your computer to factory settings. Most computers have their own recovery software that can be found by performing a search. Additionally, computers that run the Windows Operating System have a default recovery program that can also be found by performing a search.
Ahnlab Magniber Decrypt V4 10
A boot screen that can be used to access options to restore your computer can be reached by rebooting your computer and pressing the F8 key once the manufacture screen is displayed.